I’m having issues connecting securely to my Amazon S3 bucket and keep getting security or SSL errors. I can’t upload or download files because of this. Has anyone run into similar problems, and what steps did you take to fix it? I need help figuring out what’s wrong.
How I Set Up Encryption on My S3 Bucket (With Pics!)
Alright, check this out—stumbled on this while tidying up some ancient AWS setups. If you’ve ever messed around with Amazon S3 buckets, you know the feeling when you forget to turn encryption on. It’s one button but will haunt you later. Here’s my personal walkthrough for locking stuff down (with bonus Mac integration for the curious).
Locking Down Your S3 Bucket: My Steps
So, you’ve got some data chilling in S3. Maybe you’re a stickler for privacy, or your boss is giving you that “Are we secure?” look. Here’s how I did it—practically muscle memory by now:
- Roll into the AWS Console
- Log in (2FA, always), and choose your bucket.
- Hunt Down the Properties Tab
- Not even kidding, it’s like the sibling to the Overview tab.
- Find “Default Encryption”
- It’s tucked in there. Click it.
- Pick Your Poison: Server-Side, Client-Side
- You’ll get options. I usually just go server-side (SSE-S3 or SSE-KMS). But hey, if you want to encrypt before uploading, you do you.
- Smash “Save” Like It Owes You Money
- This locks in your setting for future uploads.
Pro tip: If you poke the “change” button, you’ll see if your settings are actually in effect. AWS doesn’t always trust you to remember what you did, and honestly, neither should you.
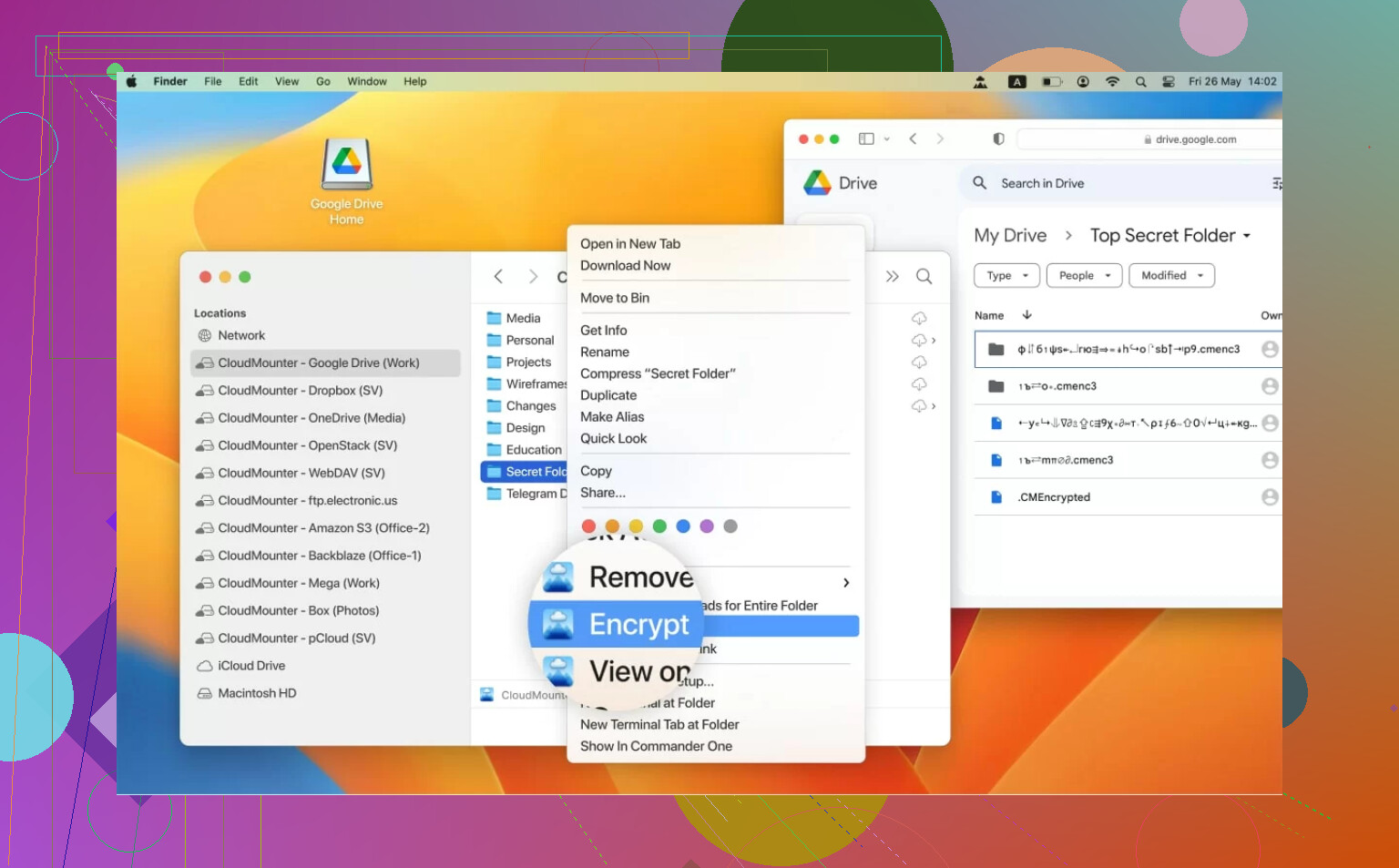
Want MOAR Layered Security? I Use CloudMounter on Mac
Let’s say you’re on a Mac (I am) and you wish your S3 cloud felt more, well, local. Like, Finder-level access. Enter CloudMounter. This gem lets you actually “mount” your S3 as a drive.
- Browse and search your cloud files as if they’re just part of your desktop.
- Bonus points: It encrypts before anything even leaves your Mac.
- Not just S3—this thing mates with all kinds of cloud services.
Honestly, it’s one of those tools you don’t realize you need until you try it, then you wonder how you lived without it. No more awkward Amazon Web UI dancing.
That’s my workflow. Anyone else encrypt their buckets differently? Do you trust AWS-managed keys, or are you rolling your own KMS and losing sleep about it? I’m nosey, drop your war stories.
SSL errors with S3? Dude, I’ve absolutely been there. It’s like AWS wants to test your sanity sometimes. Encryption is cool and all (props to @mikeappsreviewer for the thorough breakdown with screenshots!), but if you’re stuck at the “can’t even connect” phase, that’s a different flavor of pain.
Here’s my blunt checklist, straight from my own bucket battle scars:
- Is your system clock off? No, seriously. SSL hates it when your local system time drifts. Sync that shiz.
- Certificate Chain? If you’re getting errors about “could not establish trust” or some boring root CA rant, make sure your OS has the latest root certificates. macOS and Windows are usually fine, but some Linux boxes are like cryptic puzzle games.
- Endpoint Issues? Typo in the bucket region or using the wrong S3 endpoint can cause handshake fails. Double-check you’re pointing to
s3.amazonaws.comor your region-specific endpoint. - Corporate Firewall/Proxy? If you’re behind some mega-paranoid firewall (lookin’ at you, corporate IT), SSL inspection or man-in-the-middle proxies can nuke cloud connections. Sometimes switching networks or using a VPN makes it magically work.
- Client App Outdated? If you’re using something like an older S3 client, Python library, or even AWS CLI v1, SSL protocols can be out of date. Grab the latest AWS CLI or SDK and see if that fixes it.
On the topic of tools, I know @mikeappsreviewer is all-in on CloudMounter for Mac—and yeah, having Finder integration and real pre-upload encryption is amazing, especially when AWS CLI’s UX is like a slap to the face. But if you’re just testing, Cyberduck on Mac/Windows can also expose dodgy SSL settings, to see if your bucket’s doing something weird.
Contradicting a bit with default encryption advices: bucket encryption alone won’t fix SSL snafus at connection time. It just protects your data at rest. Your SSL pain is most likely about how your machine talks to AWS, not what happens after the upload.
Honestly, 80% of the SSL errors I dealt with came down to either outdated certs or my clock being like five minutes off. The other 20%? Broken endpoints and a few facepalms.
Anyone else ever had their connection suddenly work after a system update, or am I just infected with the “it works when I reboot” curse?
Okay, absolute real talk: AWS S3 SSL errors are like a rite of passage, except way less fun and nobody brings cake. Everyone here is spot-on about the clock—seriously, the number of times I’ve rage-synced my laptop because S3 said “lol, cert invalid”—but here’s where I’ll add my own chaos:
Sometimes, it’s not even your end. S3’s regional endpoints can randomly flip the bird if AWS is rolling out new certs or there’s a DNS hiccup mid-flight. If you know your certs are up to date and you still get ‘SSL handshake failed’ or ‘could not establish secure connection,’ pop open your DNS cache and flush it. I’ve legit seen this solve the issue when nothing else worked. (Windows: ipconfig /flushdns, Mac: sudo killall -HUP mDNSResponder.)
Also, not everyone loves wrappers like CloudMounter (no hate, just not my jam—I use rclone and a healthy dose of self-doubt), but if your SSL drama is only happening with one specific third-party app, try going direct with AWS CLI v2 and see if you can connect there. Sometimes apps lag behind on supported TLS versions.
Side note, somewhat controversial: I leave S3 default encryption off on my non-critical buckets so I know RIGHT AWAY if something’s failing on the client vs. AWS itself. Once stable, then I flip on SSE. Paranoid? Maybe. But troubleshooting is way easier when you isolate encryption layers from transport issues. Both matter, but only one stops you dead at the SSL start line.
And, if you’re on one of those “no self-signed certs” shops or corp laptops from the crypt, sometimes IT’s shoved their company CA in your cert store and it mucks everything up. Test on a personal device or hotspot if all else fails—network weirdness is a thing.
So yeah: check your local clock, nuke your DNS cache, try AWS CLI v2 direct, and whittle down if it’s the app or the system. Don’t trust that a recent OS update didn’t break your network stack—those ghosts are real. No shame in turning it off and on again either, just, y’know, don’t tell anyone that was the fix.
Let’s do a diagnostic cross-exam: beyond the usual suspects (clock skew, DNS trickery, cert confusion—solid callouts from previous posters), I’ve stumbled on a few less-obvious S3 SSL blockades—worth a mention if you’re still getting stonewalled.
-
Corporate Network “Helpers”: Shout-out to anyone whose work WiFi sneakily MITMs your traffic for “security”. Sometimes an S3 SSL error is your endpoint getting intercepted and re-wrapped in an untrusted company CA. Quick test: hotspot from your phone and try again. If it magically works, blame the network, not your setup.
-
Old TLS Protocols: Modern AWS endpoints require TLS 1.2+. If your client (or ancient library) is stuck on TLS 1.0/1.1, handshake just dies in silence. Upgrading SDK/CLI matters.
-
Regional Mismatches & VPC Endpoints: If your S3 bucket is locked with a VPC endpoint, but you’re not on that VPC (or your IP isn’t whitelisted), welcome to SSL purgatory. Double-check those settings—buckets now strictly enforce regional access and policy rules.
-
Proxy & Firewall Oddities: HTTP proxies or SSL inspectors in the route? Can mangle cert chains during negotiation. Try direct, sans-proxy, to verify.
For cloud-native die-hards: I see the love/hate for things like rclone and S3 CLI—nothing wrong with going CLI-first for troubleshooting, but GUI fans might vibe better with CloudMounter for making S3 feel like a local drive (though, heads up: it’s payware, and for non-Mac/Linux/Win, your luck’s out). Upside? Encrypt-on-the-fly and Finder integration are genuinely handy. Downside? Dependency on third-party support, and if AWS ever tweaks their auth APIs, you might wait longer on a patch compared to updating CLI tools yourself.
Honorable mention to previous suggestions from other forum friends: if your priority is “see all the debug,” stick with CLI. If “mount and go” is your speed, CloudMounter is smooth. I wouldn’t fully trust only AWS-managed keys—by all means, if you’ve got compliance needs, self-manage (KMS), but as always: that’s a rabbit hole full of trade-offs (see: sleep loss).
People also ask: Is CloudMounter safer than direct AWS CLI? Depends on your threat model and OS habits. CLI = more manual control, CloudMounter = seamless experience with a dash of blind trust in a vendor. Both have their niche, and let’s not forget there are competitors out there if you prefer other flavors. Test, reboot, and above all—I beg you—sync that system clock.